Live Threat Blocking Demos
Watch real-time protection in action
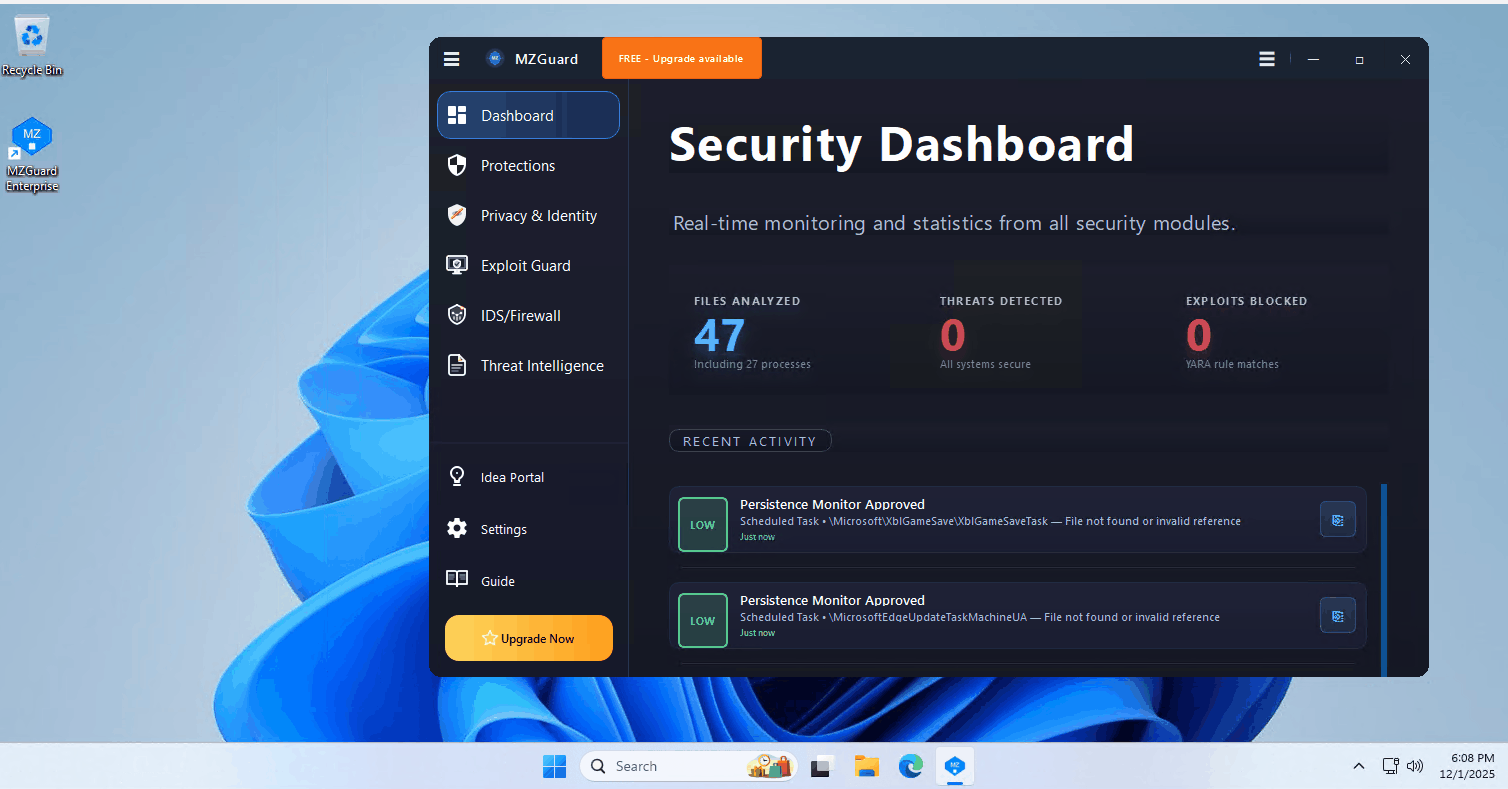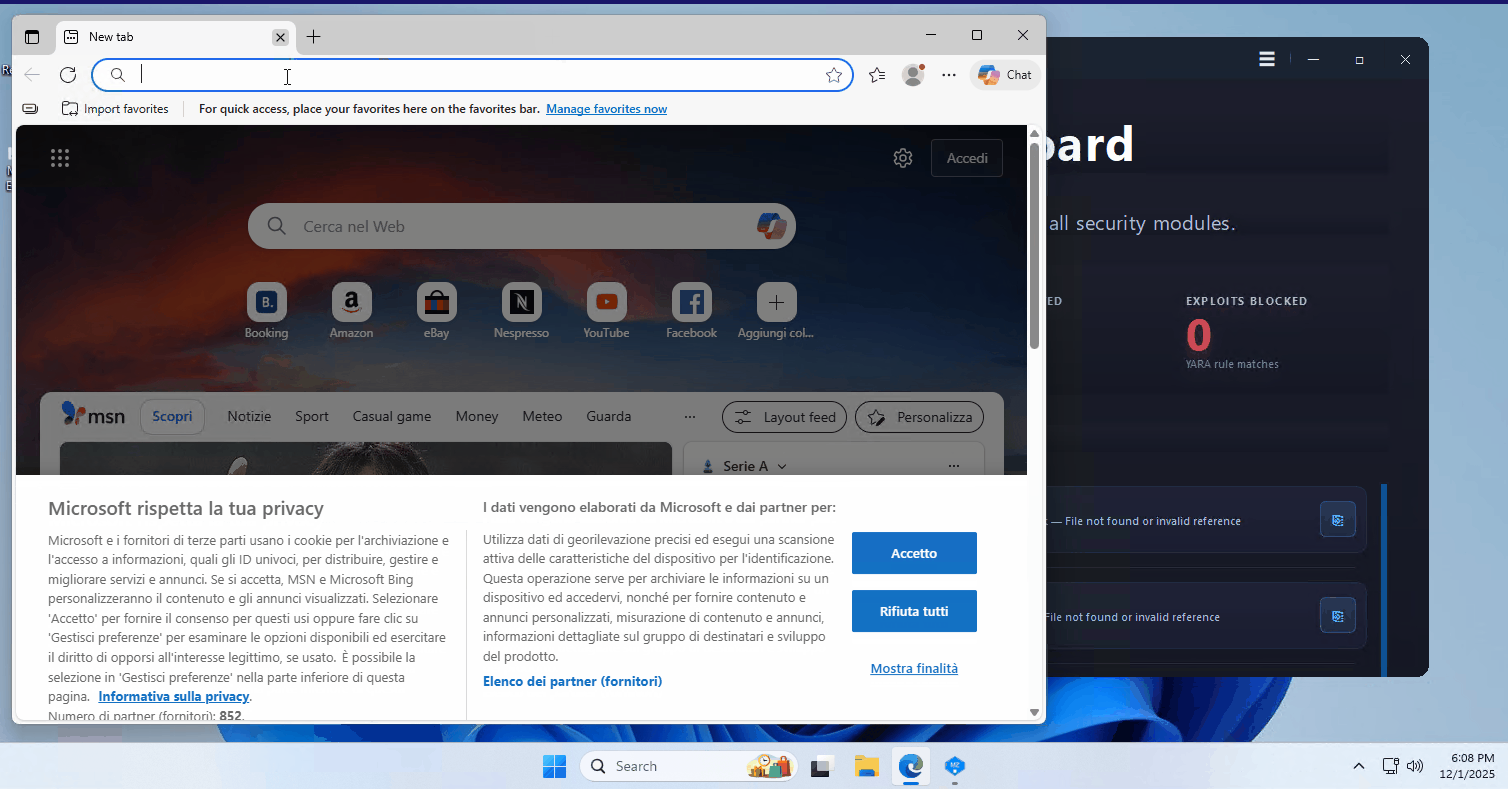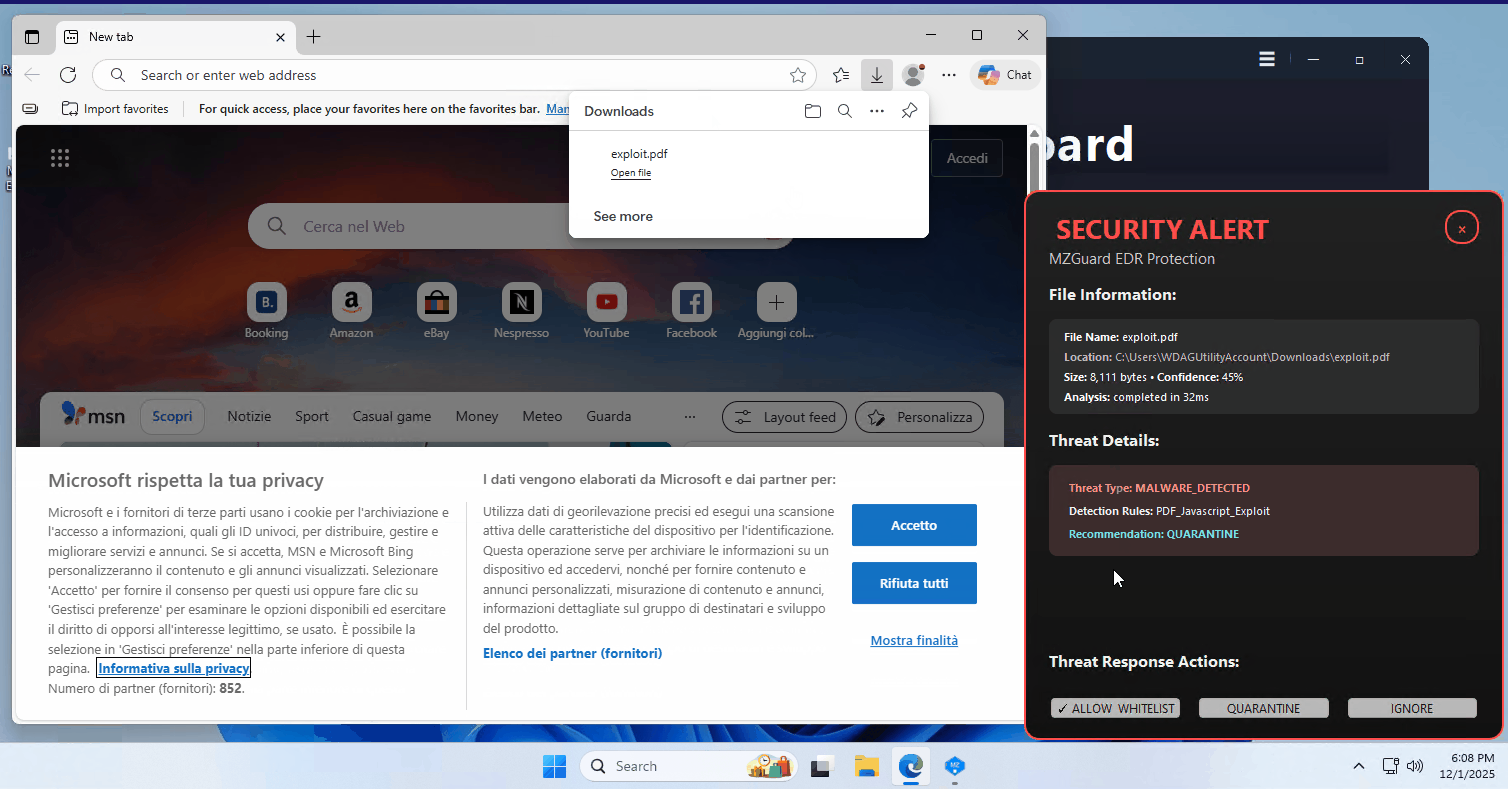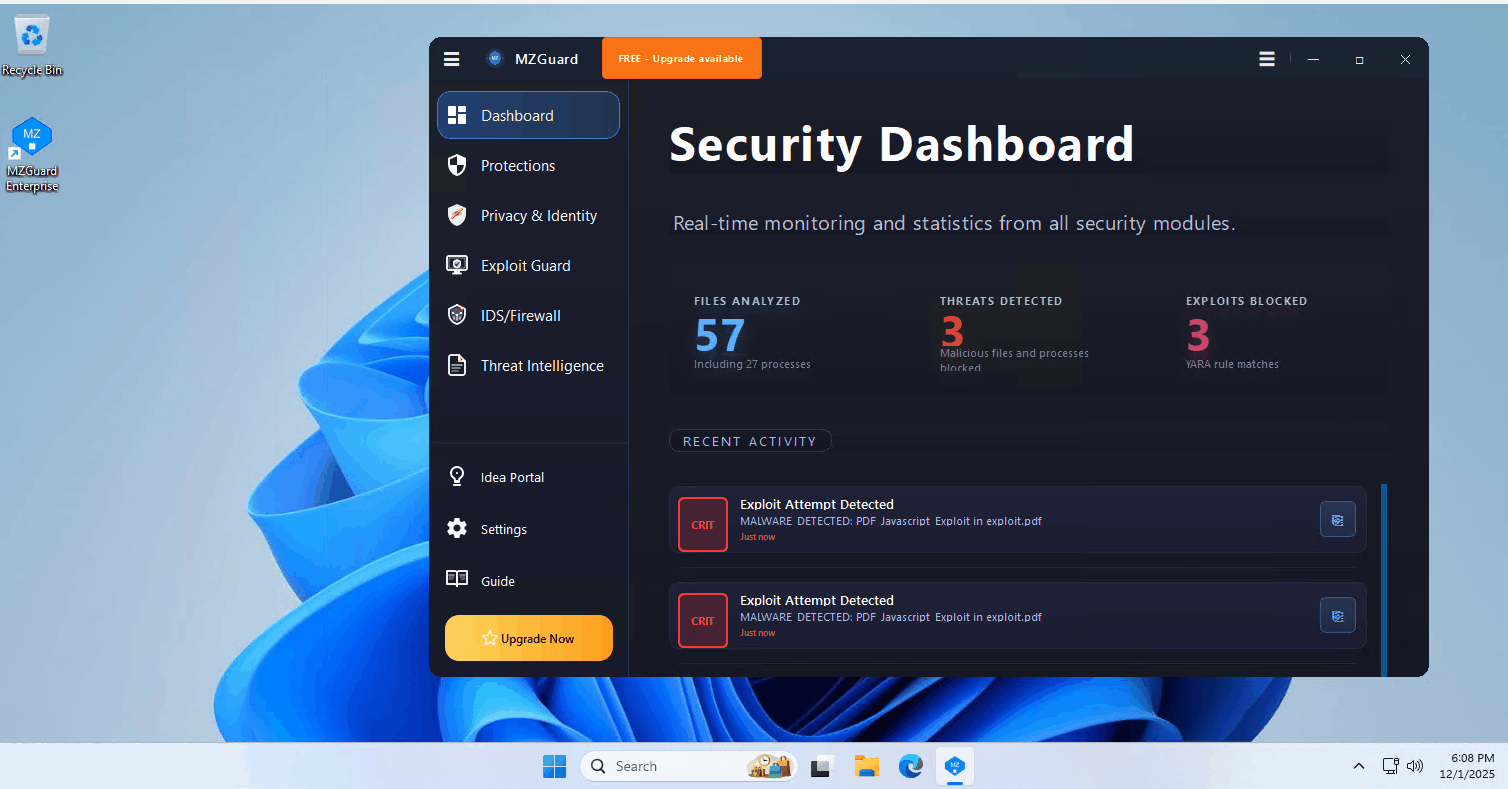
Anti-Keylogger Protection
Noise injection confuses keyloggers on banking and password managers. User consent required for each detection.

Exploit Guard & Process Monitor
YARA-driven checks for exploit indicators, suspicious payload patterns, and risky process behavior — designed for fast, explainable alerts.
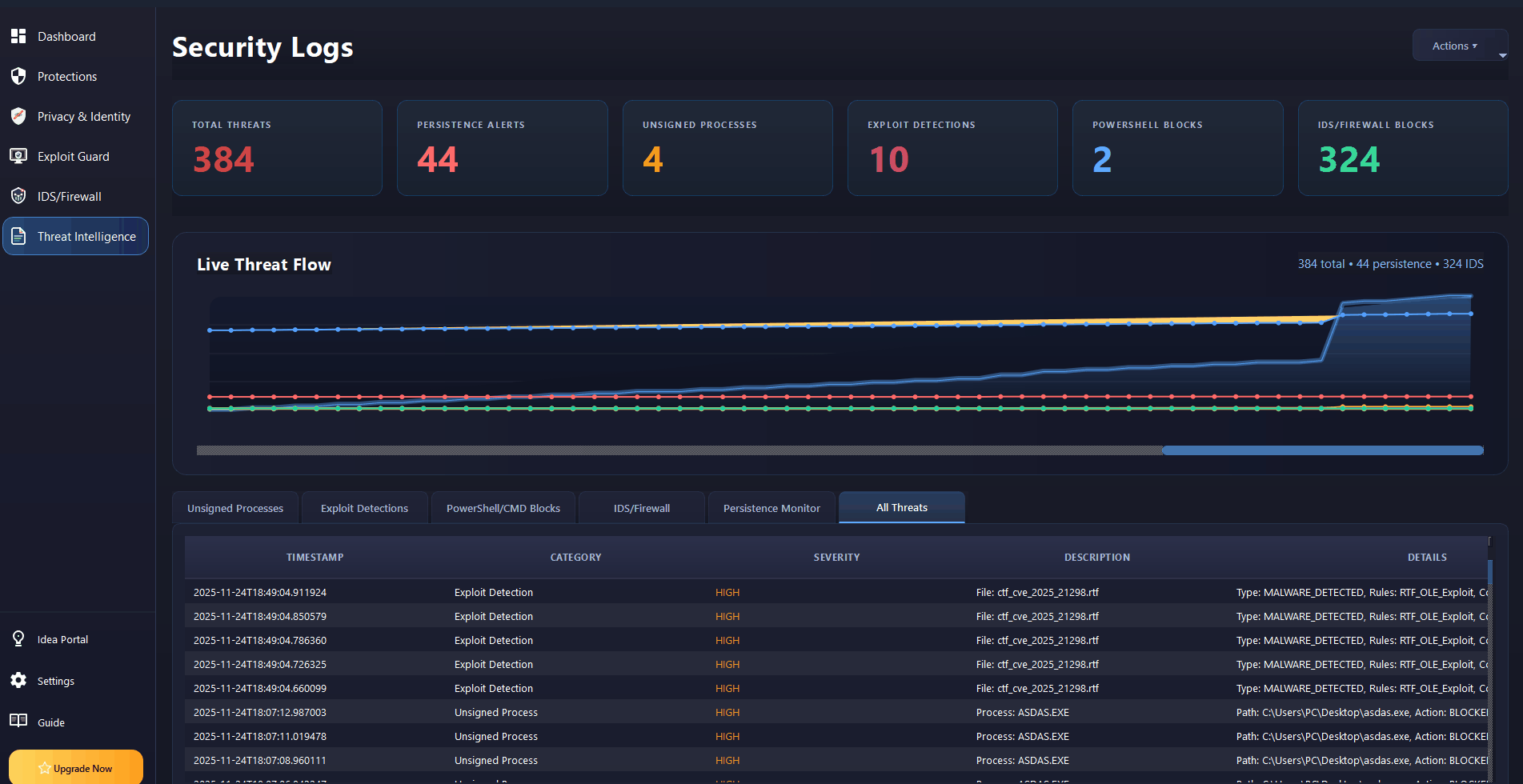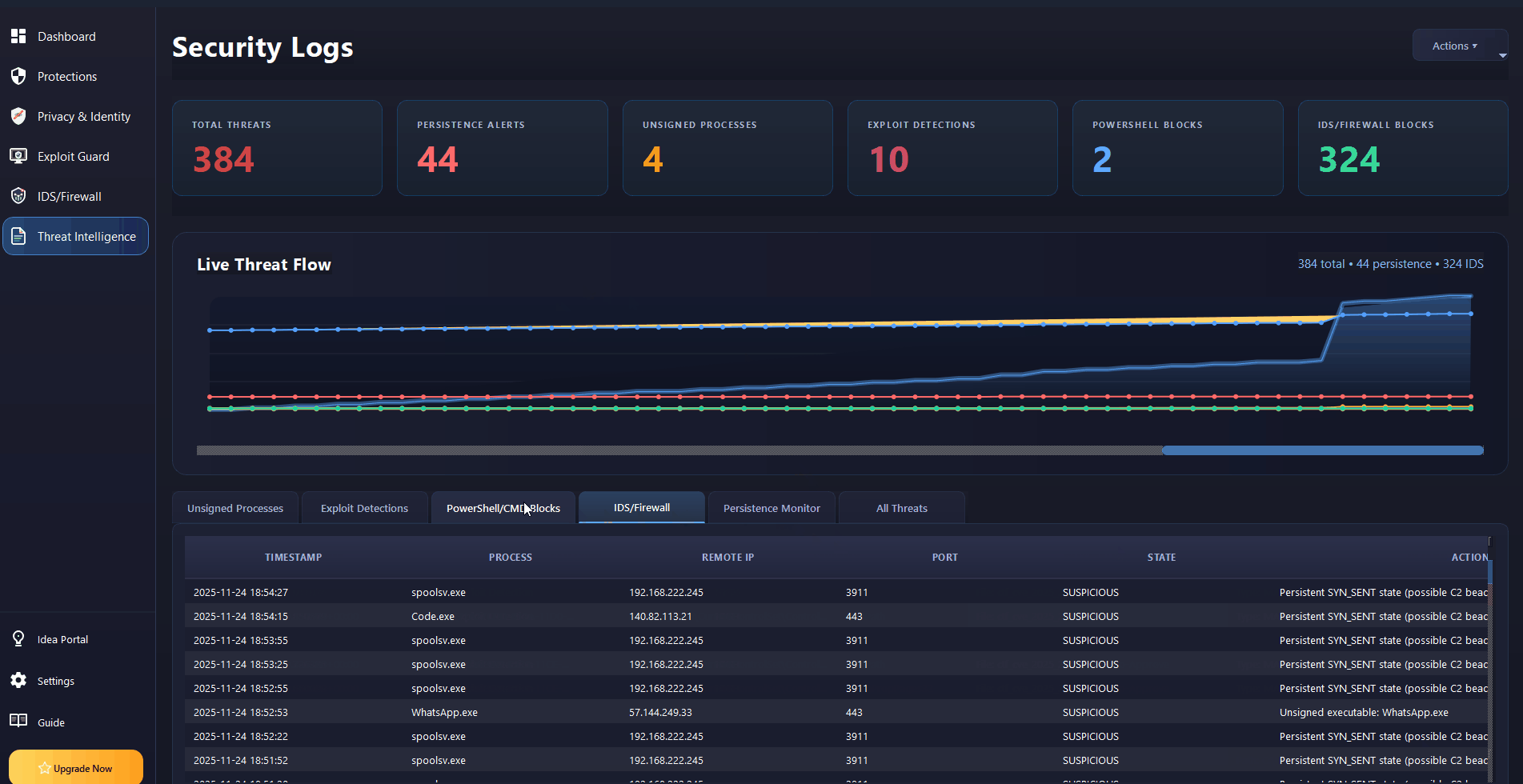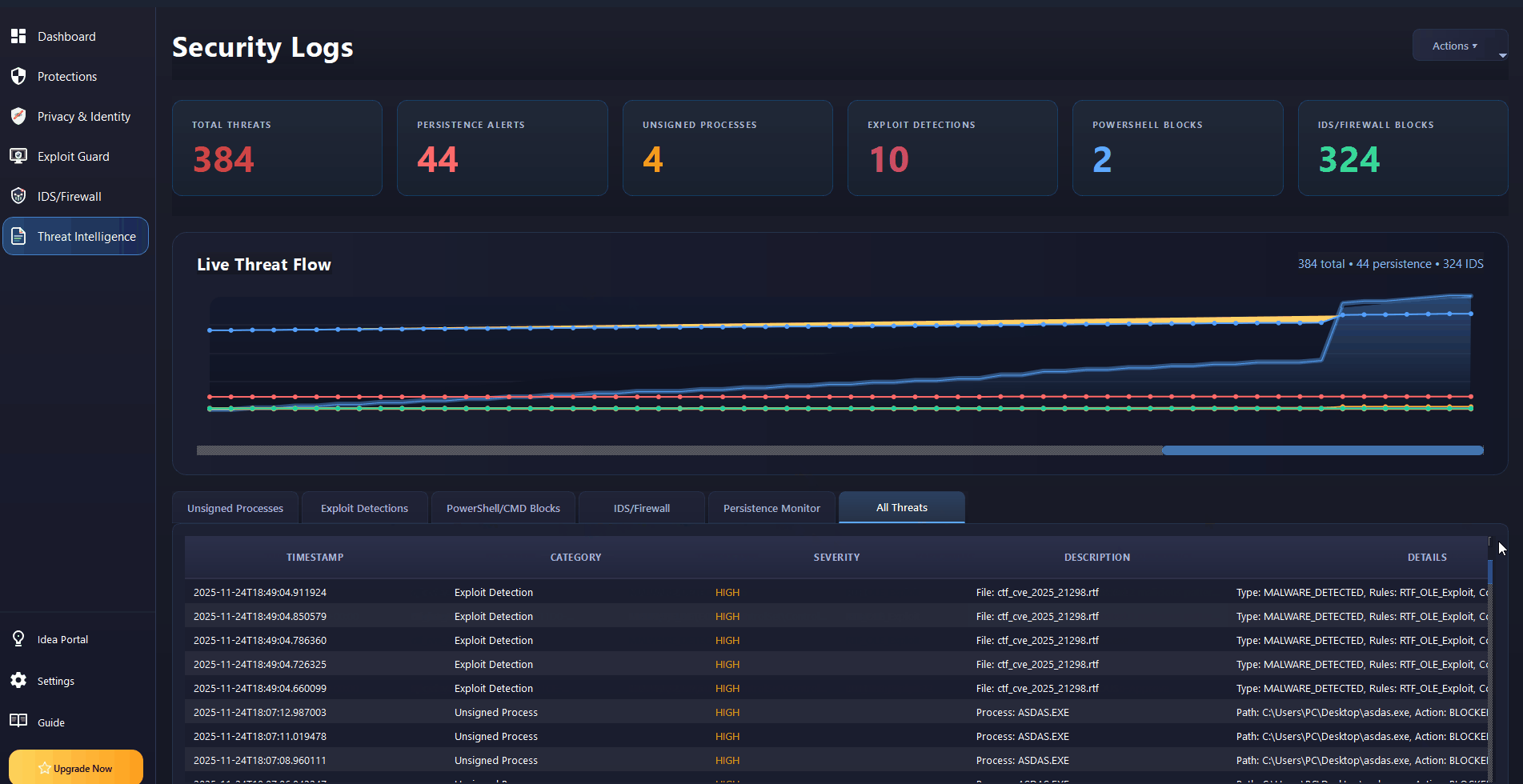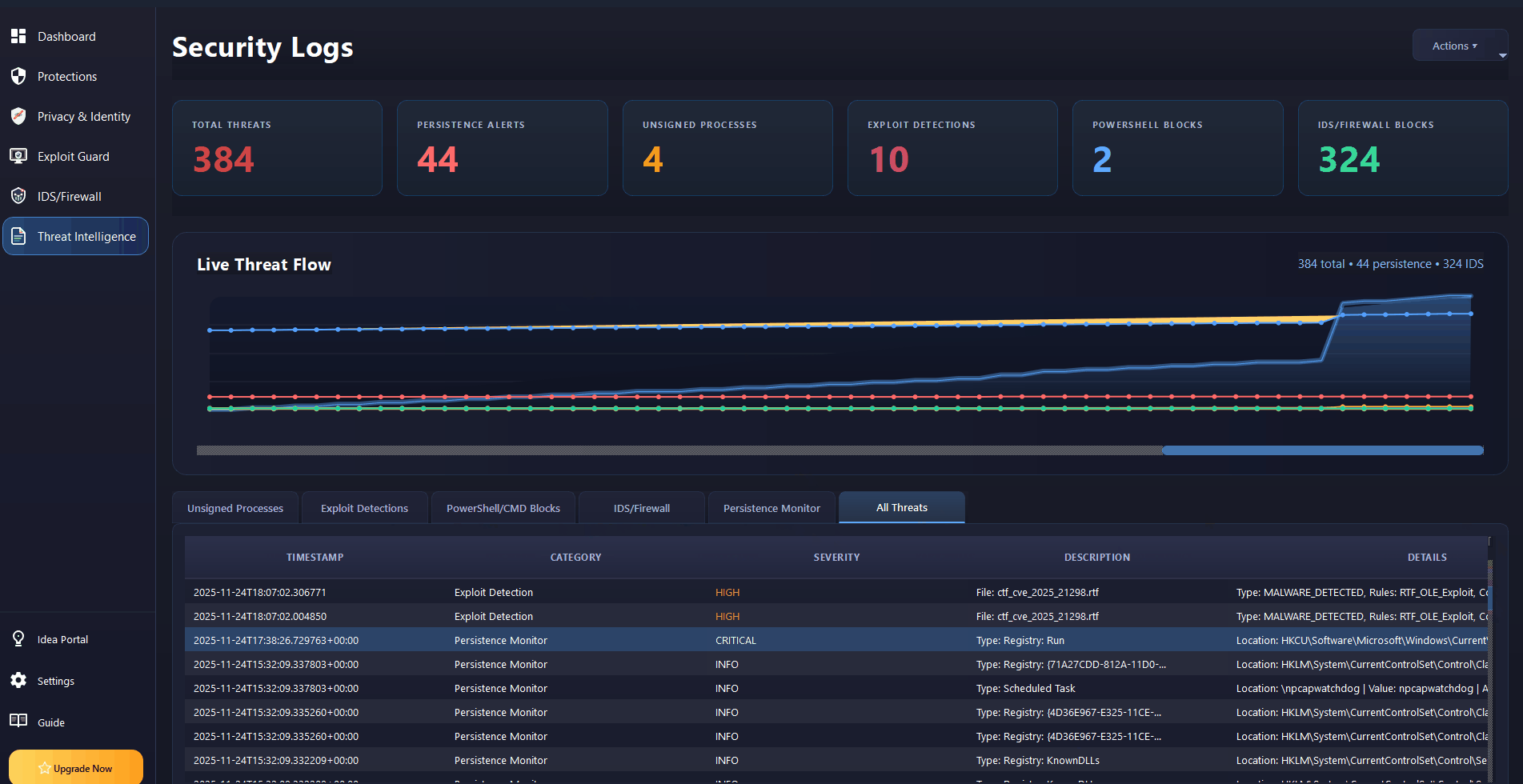
Real-Time Threat Intelligence
Live threat flow visualization with persistence monitoring, PowerShell blocking, and IDS/Firewall integration.